Manage credentials
Atlan automatically manages and secures authentication data for your applications through a comprehensive credential management system. When your applications need to connect to external systems, Atlan handles the complexity of storing, protecting, and retrieving credentials—you simply provide the authentication details through the UI, and Atlan ensures they remain secure throughout the entire application lifecycle using credential GUIDs as secure references.
Core components
Atlan's credential management integrates several specialized components that work together to protect sensitive authentication data:
Credential GUIDs
Unique identifiers that reference securely stored credentials without exposing actual sensitive data
Secret Store
Secure vault system that stores and protects credential data
State Store
Configuration database that stores workflow settings with secure GUID references
Runtime Resolution
Automatic credential retrieval only when needed, with in-memory processing
How Atlan manages credentials
Atlan follows a secure, multi-phase process that ensures credentials are protected throughout their lifecycle:
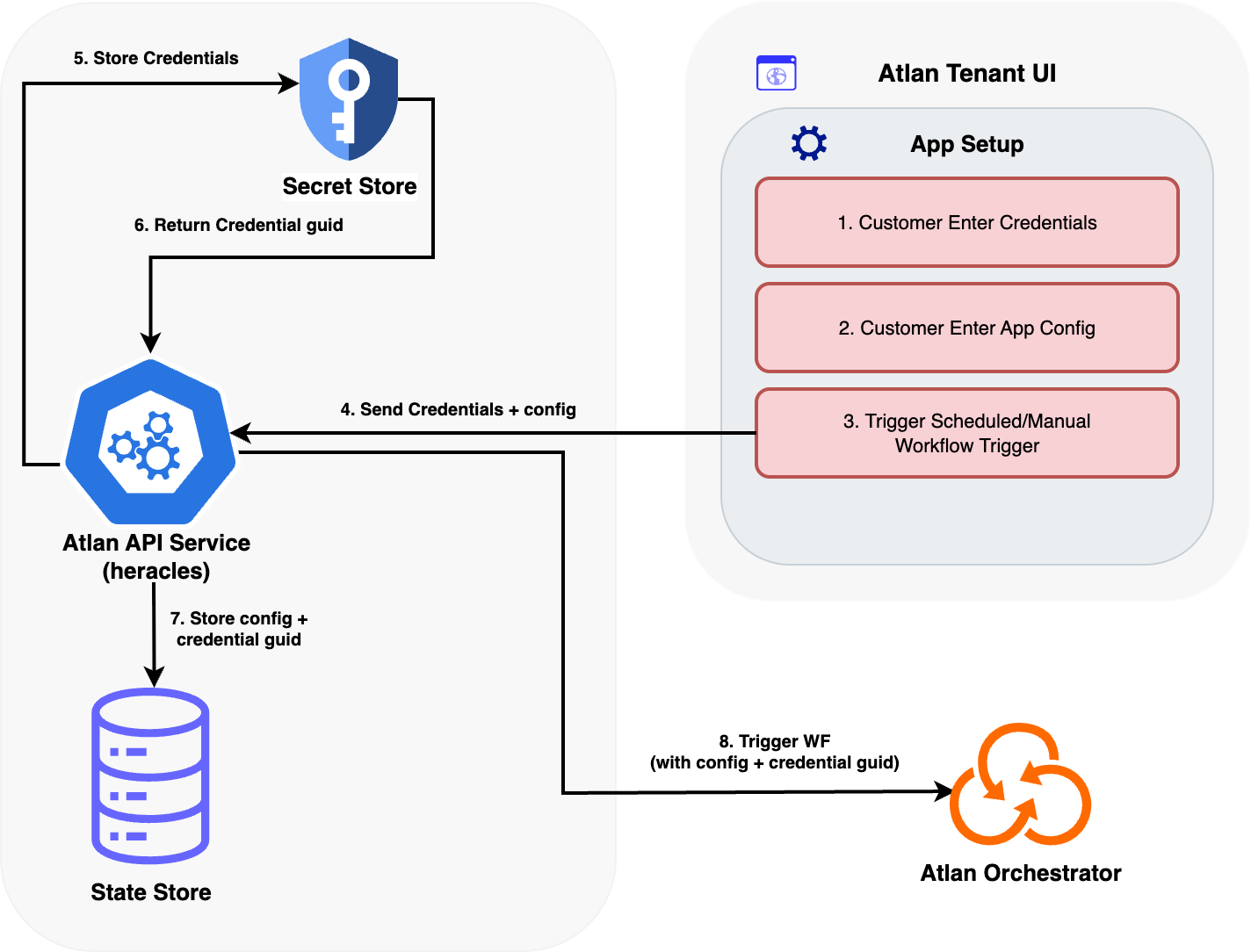
Configuration phase
The process begins when you configure an application that requires external authentication:
- Customer enters credentials: You provide authentication details through secure UI fields in the Atlan Tenant UI application configuration page
- Customer enters app configuration: You define non-sensitive settings like connection parameters, workflow schedules, and application behavior (including any metadata from fetch operations)
- Trigger workflow: You initiate workflow execution, either manually or based on a predefined schedule
Secure storage phase
Once credentials are provided, Atlan automatically handles secure storage and reference creation:
- Send credentials + config: The Atlan Tenant UI sends both credentials and application configuration to the Atlan API Service (Heracles)
- Store credentials: The Atlan API Service stores the credentials in the Secret Store vault
- Return credential GUID: The Secret Store generates and returns a unique credential GUID reference to the Atlan API Service
- Store config + credential GUID: The Atlan API Service stores the application configuration in the State Store with:
- Workflow configuration containing only non-sensitive parameters (host, port, metadata)
- A reference to the credential GUID rather than embedded credentials
- Credential configuration indexed separately by the same GUID for secure isolation
Runtime resolution phase
During workflow execution, Atlan handles credentials securely through runtime resolution:
-
Trigger workflow: The Atlan API Service triggers the workflow execution with the Atlan Orchestrator, passing only a minimal payload:
{
"workflow_id": "atlan-redshift-1756943536"
}This ensures that sensitive data is never passed as workflow input—only the workflow identifier is transmitted.
- The Orchestrator automatically retrieves the workflow configuration from the State Store using the workflow ID through the
get_workflow_configactivity - When the application needs authentication, it uses
SecretStore.get_credentials()to resolve the credential GUID into actual credentials - Credentials remain only in memory and are never persisted
- The Orchestrator automatically retrieves the workflow configuration from the State Store using the workflow ID through the
This phased approach ensures credentials are never exposed in configuration files, logs, or during transport—maintaining security throughout the entire application lifecycle.
How credentials remain secure
Atlan's credential management system implements multiple layers of security to protect sensitive data:
- Storage isolation prevents exposure: Separating credentials (Secret Store) from configuration (State Store) ensures a configuration breach never exposes passwords. Access to the State Store reveals only GUID references.
- GUIDs can't be reverse-engineered: These opaque identifiers reveal nothing about the underlying credentials. A GUID like
abdf-1244provides no information about the actual password, making logs and configs safe to share. - Memory-only runtime access: Credentials exist in memory only during active use and are never persisted to disk. This reduces the exposure window compared to traditional credential caching.
- Audit without exposure: Every credential access is logged using the GUID reference—never the credential values themselves. This provides tracking without security risk.
- Reduced security burden: Atlan handles encryption and secure storage automatically
- Developer productivity: Simple APIs hide security complexity
- Operational reliability: Automated management eliminates manual credential handling errors
See also
- Apps framework: Understand the broader application development ecosystem
- Application architecture: Learn about the technical architecture of secure applications
- Retrieve credentials - Use SecretStore to resolve credential GUIDs into actual credential values during workflow execution